Home 2012
Yearly Archives: 2012
Building Image Processing Embedded Systems using Python, Part 1
The first part of this three-part series gives a brief overview of the embedded vision and the various components required to make it work....
IPsec VPN Penetration Testing with BackTrack Tools
This article outlines the value of penetration-testing VPN gateways for known vulnerabilities and also shows you how to prevent a breach into the internal...
Guard Your Network with IPCop, Part 2: Add-ons
A basic installation of IPCop provides minimum firewall functionality such as a proxy, compatibility with various Internet connections, port forwarding, IPSec VPN, etc. To...
Cyber Attacks Explained: Network Sniffing
In earlier articles in this series, we have explored denial of service attacks and packet spoofing. This month, let us focus on a wider...
CodeSport
In this month's column, we take a short break from our discussion of compiler optimisations and feature a set of questions for computer science...
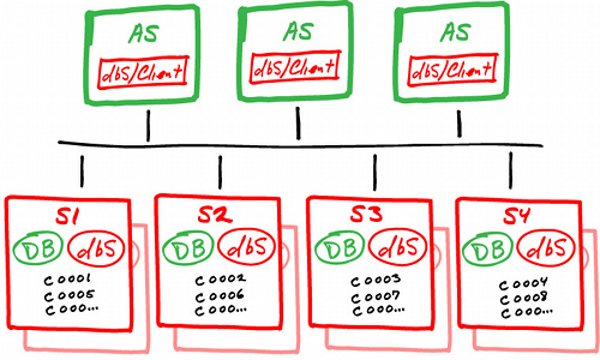
NewSQL — The New Way to Handle Big Data
Big data, big data, big data! This term has been dominating information management for a while, leading to enhancements in systems, primarily databases, to...
FOSS is __FUN__: Get the Basics Right
A few thoughts about databases in general... and some rants about the good old ways.
There are a plethora of free/open source databases around, from...
Joy of Programming: Understanding Bit-fields in C
One important feature that distinguishes C as a systems programming language is its support for bit-fields. Let us explore this feature in this column.
In...
The Importance of In-memory Databases
It has been predicted that in-memory computing will be one of the Top 10 technologies of 2012. In-memory databases (IMDBs) are a critical part...
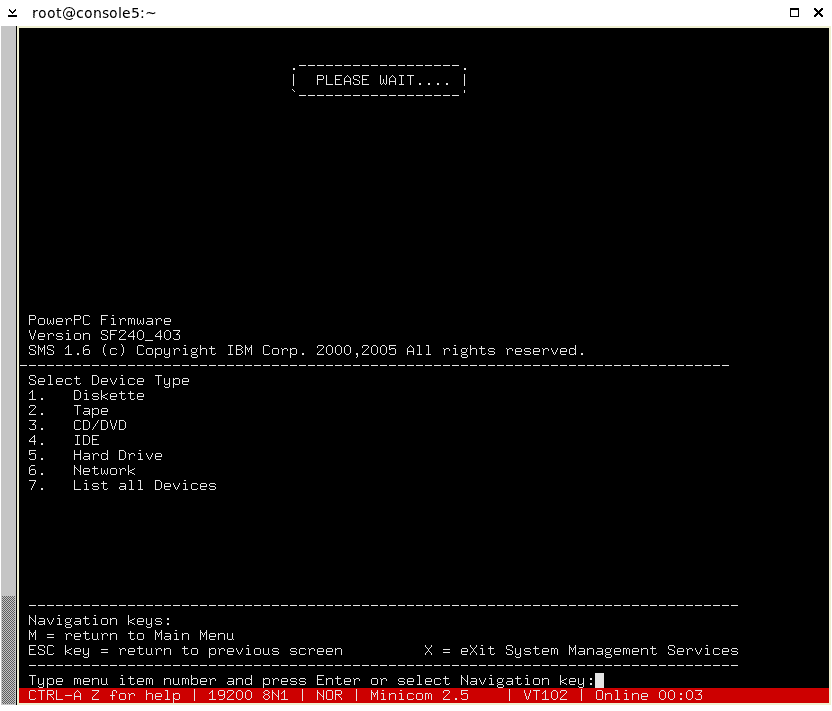
Linux on POWER
Anyone familiar with GNU/Linux will not be surprised by the fact that this operating system runs on almost all known processors. However, very few...