
Many commercial encryption products can protect files, folders and partitions. Probably the most discussed is “Bitlocker”, which is bundled free with MS Windows 7 Ultimate. And if you have ever wondered if there is open source encryption software — there is and it’s called TrueCrypt.
As mentioned on TrueCrypt.org, it is a software system to establish and maintain an on-the-fly-encrypted volume (data storage device). On-the-fly implies that data is automatically encrypted right before it is saved, and decrypted right after it is read, without user intervention. No data stored on an encrypted volume can be decrypted without the correct password/keyfile(s) or correct encryption keys. The entire file system is encrypted.
Files can be copied to and from a mounted TrueCrypt volume just like with any normal disk (for example, by simple drag-and-drop operations). The software works as expected, is simple, and has a GUI for ease of use. Apart from these properties, I would say that its most important feature is the security TrueCrypt offers. It’s so secure that even FBI hackers failed to recover data from TrueCrypt encrypted volumes. Surprised? Here are some more facts: it is available under the GPL, works on almost all operating systems, including Linux, Mac OS and MS Windows 2000, and later versions.
Continue reading at your own risk… you may soon fall in love with TrueCrypt!
The basics of encryption
So let’s take a quick look at the basics of encryption. Everybody knows what a password is, and how it operates. Anybody can visualize encryption key to be same as the password. However, technically, there are a few differences. Look at the following table for a comparison.
| Password | Encryption key |
| Typically, a combination of a few characters to be entered before gaining access. | A combination of characters, generally slang or a pass-phrase or random character sequence required to decrypt the message. |
| Does not change the contents of the original resource. | Is used to actually change the data by using encryption techniques. |
| If lost, protection can typically be removed with ready-made tools such as spreadsheet and document password crackers/removers, to reveal the actual data. | It is practically impossible to retrieve (decrypt) data from an encrypted file unless the key is known. The only way is brute force, which can also be ineffective for a key with sufficient strength. |
(Be careful — lose the encryption key, and you lose all the data!)
Basically, there are three encryption mechanisms: the symmetric key, asymmetric key and hashing. For this article, we need to understand two of them.
Symmetric key encryption converts data from clear text (original format) to cipher text (encrypted format) using an encryption algorithm and an encryption key. The same key is used to convert encrypted data back to clear text. To keep data safe, one must guard the key.
A hash algorithm is used on data to produce a unique value (a string of unique characters). If the same algorithm is used on modified data, the generated checksum differs, thus confirming the loss of original data integrity. One important property of the hash value is that it cannot be used to recreate the original data.
TrueCrypt uses both these functions: symmetric key encryption and a hash algorithm. Now, let’s understand more about TrueCrypt.
Installation
Download the latest stable version available, which is 7.1, for your OS. The basic installation is simple and straight forward; I will walk you through the steps for SuSE 11.1.
Untar the downloaded binaries and launch the setup. Proceed through various screens and complete the installation by accepting the license. The application browser will show the installed package.
Usage
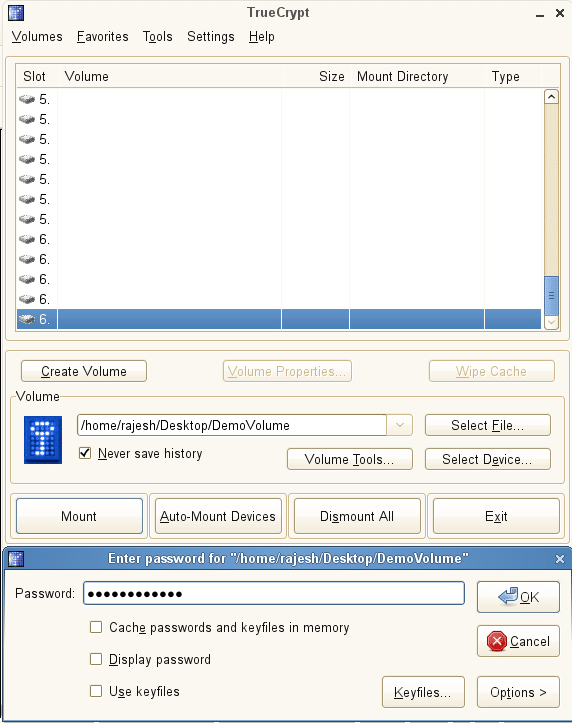
Launch TrueCrypt, select a slot and click the Create Volume button to launch the volume creation wizard. After selecting Standard TrueCrypt Volume, enter the desired filename (DemoVolume), as shown in Figure 1.

Next, select the location where you wish to create the volume. The next screen asks you to select the encryption and hash algorithms. (You may also select a combination of algorithms.) To estimate the encrypted file write speed, you may want to benchmark your system. The test machine had 49 and 51 MBps encryption and decryption speeds.
Select the desired encryption and hash algorithm, followed by the volume size, as required. To create DemoVolume, I chose AES encryption SHA-512 hash and the size of 10 MB. Continue and provide a strong pass-phrase (I used KhulJaSimSimkhuljasimsim), choose the filesystem type, and format the volume.
Mount this volume (see Figure 2) by selecting DemoVolume and entering the corresponding pass-phrase. The mounted volume will be accessible just like any other. Files can be copied to it with a file browser. Once data is copied, simply dismount this volume. Your data is now saved in a TrueCrypt encrypted volume file, which you can email, copy on a pen drive, or even synchronise with cloud-based storage services.
You can use this tool to encrypt complete partitions, a pen drive or any data storage device to secure your data, just like creating a new volume of the required size. Do use this utility, and let your friends know about it. Also, do consider making a donation to this fantastic project.
















































































Secured flow ……
[…] TrueCrypt — Learn the Art of Encryption […]
software is the best
software is the best
I prefer LUKS (DMCrypt) on Linux. Truecrypt is way too slow.
The best !!!