
Steganography and cryptography have been widely used to hide sensitive information. This article offers a brief introduction to how both these methods can be used together. The implementation uses Python with the Stepic and ezPyCrypto libraries.
Cryptography is “the practice and study of hiding information.” The word is a combination of the Greek kryptos (“hidden”) and grápho (“I write”). Early cryptography was solely concerned with message confidentiality — making the message unreadable by interceptors, by encoding it with a key. Modern cryptography includes techniques for message integrity checking, sender/receiver identity authentication, digital signatures and more.
Algorithms that use the same key for both encryption and decryption are known as symmetric key algorithms. This practice, invented in the 1970s, uses a pair of keys — one to encrypt, the other to decrypt. Users of this technology publish their public key, while keeping their private key secret. This enables anyone to send them a message encrypted with the public key, which only the holder of the private key can decrypt. These algorithms are designed so that finding out the private key is extremely difficult, even if the corresponding public key is known to an attacker.
Steganography means “covered writing” in Greek; it is the science of writing hidden messages so that no one besides the sender and intended recipient suspects there is a message — security through obscurity. Digitally, information could be hidden in computer files (a document file, image file, program, etc) or transport layers. For example, a sender might take an image file and adjust the colour of every fiftieth pixel to indicate a letter of the alphabet. Someone not specifically looking for this kind of modification is unlikely to notice it.
Later in the article, we will see how steganography can be made far more useful by combining it with cryptography — thus, if the hidden message is discovered by an eavesdropper, they still have the burden of trying to decrypt the message.
The platform
Python, itself a flexible and productive programming language, has the popular libraries ezPyCrypto and Stepic available. ezPyCrypto is a very simple API for military-grade cryptography in Python. It encrypts and decrypts arbitrary-sized pieces of data like strings or files with asymmetric key cryptography.
Stepic provides a Python module and also a command-line interface to hide arbitrary data within images. It slightly modifies the colours of pixels in the image to store the data. These modifications are imperceptible to humans but can be detected by programs.
Setting up the libraries
Practically all Linux distributions will have Python installed, or available as installable packages. If you need to install Python itself, visit the References section for a URL.
Download the ezPyCrypto-0.1.1.tar package and run these commands as the root user:
# tar xvf ezPyCrypto-0.1.1.tar # cd ezPyCrypto-0.1.1 # python setup.py install
To set up Stepic, you need to install related package: Imaging-1.1.6.tar.gz (the Python Imaging Library). To use the show() method of the PIL Image class, we need to install the xv utility, which in turn needs the libpng library package.
First set up PIL — download the Imaging-1.1.6.tar.gz archive, and (as the root) run the following:
# gunzip Imaging-1.1.6.tar.gz # tar xvf Imaging-1.1.6.tar # cd Imaging-1.1.6 # python setup.py install
Next, download Stepic, and run the following commands as root:
# tar xzf stepic-0.3.tar.gz # cd stepic-0.3 # python setup.py install
Steganography with Stepic
Stepic’s Steganographer class is now deprecated in favour of directly-callable functions in the module. (Refer to he API documentation for the module.)
- Start the Python interactive shell:
$ python
- Import PIL’s Image, and the stepic module:
>>> import Image, stepic
- Open an image file in which you want to hide data:
>>> im=Image.open ("lena.jpg") - Encode some text into the source image. This returns another Image instance, which you need to save to a new file:
>>> im2=stepic.encode(im, 'This is the hidden text') >>> im2.save('stegolena.jpg','JPEG') - Display both the images (with and without hidden data) to see if there is any visible change:
>>> im2=Image.open ("stegolena.jpg") >>> im2.show() >>> im.show()
Use the decode() function to extract data from an image:
>>> im1=Image.open('stegolena.jpg')
>>> s=stepic.decode(im1)
>>> data=s.decode()
>>> print data
This is the hidden text
Hiding encrypted data inside images
Instead of hiding plain-text data in images, let’s encrypt that data (with the ezPyCrypto module) before hiding it. Since Stepic accepts data in ASCII format, after encrypting data, we need to convert it to ASCII format.
- Import modules into the interactive shell:
>>> import Image >>> import stepic >>> import ezPyCrypto
- Open an image in which you plan to hide data:
>>> im=Image.open("lena.jpg") - Create an encryption key and encrypt the message to ASCII format:
>>> k=ezPyCrypto.key(2048) >>>enc=k.encStringToAscii('This is the hidden text') - Hide this encrypted message in the image, and save as a new file:
>>>im1=stepic.encode(enc) >>>im1.save('stegolena.jpg','JPEG')
The statements shown above are the bare bones of the procedure; we have omitted some commands that you will see in Figure 1, which displays the encrypted data, and the image files before and after hiding data.
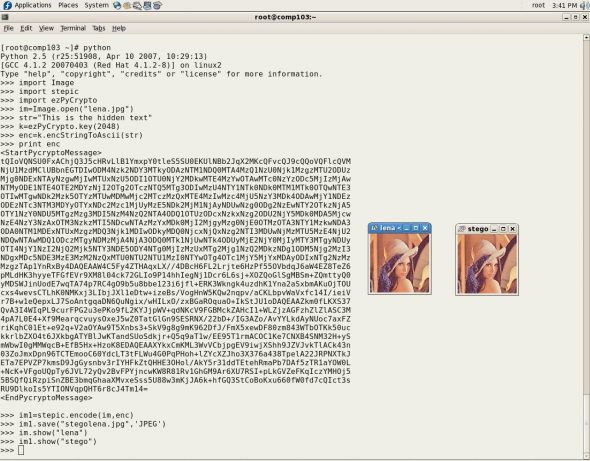
Extracting and decrypting the hidden message
Note: Create the decryption key based on the same number you used when encrypting the data.
>>> import Image, stepic, ezPyCrypto
>>> im=Image.open("stegolena.jpg")
>>> data=stepic.decode(im)
>>> k=ezPyCrypto(2048)
>>> dec=k.decStringFromAscii(data)
>>>print dec
This is the hidden text
Here, we’ve used secret-key cryptography, where the same key is used by the sender and receiver. You could also use public-key cryptography with ezPyCrypto, but that is outside the scope of this article.
References
- Jain Ankit, Steganography: A solution for data hiding
- Robert Krenn, Steganography Implementation & Detection
- Christian Cachin, Digital Steganography
- James Madison, An Overview of Steganography
- Neil F. Johnson, Sushil Jajodia, Exploring Steganography: Seeing the Unseen
- Max Weiss, Principles of Steganography
- T. Morkel, J.H.P. Eloff, M.S. Olivier, An Overview Of Image Steganography
- Andreas Westfeld and Andreas Pfitzmann, Attacks on Steganographic Systems














































































Thank you. It works with png, not jpg images for me
Don’t try this with a jpg. The text is completely wrong it doesnt work with jpg and I completely wasted about an hour messing around with this when if the idiot who wrote it had run it once he would have seen the error message telling him that it doesn’t work with JPEGS.
Run in other format?
You should publish a article regarding How stepic works for. Like how Encode and Decode functions work.
Thumbs up.
Here stepic will only accept the ascii value then how your “This is hidden Text” message is working???