You don’t need to read a book to understand why vulnerabilities in systems can put them at potential risks. Vulnerabilities may exist in your network due to misconfigured or unpatched systems. This brings us to the subject of vulnerability assessment and management—a process of identifying the presence of vulnerabilities and reducing the security risk of your system to an acceptable level.
There are various assessment tools that assist IT security professionals in identifying vulnerabilities in servers and desktops. You can initiate a scan and identify potential network and system weaknesses using vulnerability scanners. These security scans can run either on remote or local systems against target systems.
Challenges in the current scenario are:
- The non-availability of open source vulnerability assessment tools
- Understanding the architecture of VAS (vulnerability assessment systems)
- Implementing a VAS tool.
VAS architecture
Typically, the design of a VAS should meet the following basic requirements:
- Configured to reach all target systems
- Authenticated access to the VAS server and sessions
- A constant updating of the VAS plug-in database before initiating a scan
- Defining a scan frequency and ear-marking the target systems that fall within the scope of scanning
- Ensuring secure availability of scan reports with time stamping.
OpenVAS—Open Vulnerability Assessment Scanner, a fork of the now closed-source Nessus security scanner—is an open source vulnerability assessment tool. It works on a client-server architecture, which has the following four components:
- OpenVAS server
- OpenVAS feed server
- OpenVAS client
- Target systems
The OpenVAS server requires to be configured in a manner to fetch updates or the latest plug-in feeds from the publicly-hosted OpenVAS Feed Repository server. The OpenVAS server will contact the repository server to identify available updates and download them.
The OpenVAS client is a GUI client used to manage, configure and report scan results. Access to the OpenVAS server is controlled by a secure password- or certificate-based authentication. Through the OpenVAS client software you can specify target systems, port range, NVT (network vulnerability test) and initiate the scan. The OpenVAS client will show you the real-time status of your scan and report the relevant results. You can manage various scans by grouping IP addresses based on category and saving them in separate sessions. Results under each session are stored in that particular session and kept separately.
After you initiate your scan, the OpenVAS server will have attack traffic between it and the target systems. OpenVAS will initiate port scans and network vulnerability tests on target systems to identify potential weaknesses in systems.
Components
Let’s look more closely into the four components of OpenVAS:
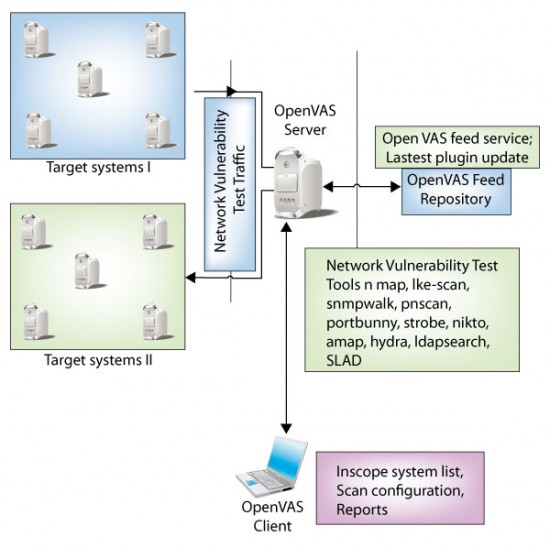
- OpenVAS Server: This is the main component of OpenVAS, which is connected via a GUI-based client in order to scan target systems. Server and client communication only include configuration and scan initialisation traffic. Actual scan traffic (network vulnerability test traffic) flows between the server and target systems (as shown in Figure 1). The server has four components: openvas-libraries, openvas-libnasl, openvas-server and openvas-plugins.
- OpenVAS Client: This is a GUI- or terminal client-based application that is used to establish and initiate network vulnerability tests against target systems. The client connects to the server by authenticating itself either using a password or a certificate. The client is a successor of NessusClient.
- OpenVAS NVT Feed: NVT stands for network vulnerability tests. These are signature files that are available as plug-ins on the OpenVAS repository server. By default, the OpenVAS Server is configured to fetch plug-in updates from the repository server.
- OpenVAS LibNASL: The NVTs are written in the Nessus Attack Scripting Language (NASL). This module contains the functionality needed by the OpenVAS Server to interface with NASL.
Tools
OpenVAS Server is integrated with lots of powerful open source software, ranging from network to application security toolkits. The following table lists various tools that have been integrated with OpenVAS.
| Tool | Description |
| nmap | A powerful port-scanning tool that scans remote hosts for open TCP/UDP ports. |
| ike-scan | A strong VPN fingerprinting and enumeration tool that can list the encryption, users and vendor. |
| nikto | A Web server scanner that can perform comprehensive tests against servers to identify Web application weaknesses. |
| hydra | A network login cracker. It can do a dictionary-based attack on log-in IDs. |
| snmpwalk | An SNMP application that uses SNMP GETNEXT requests to query a network entity for a tree of information |
| amap | An application protocol detection tool that is independent of TCP/UDP port. |
| ldapsearch | An LDAP utility that is used to perform search operation on an LDAP server by opening and binding a connection to an LDAP server using specified parameters. |
| pnscan | It’s another port scanner plug-in that’s available. |
| portbunny | A Linux kernel-based port scanner that aims to provide TCP-SYN port scanning. It can do sophisticated timing, based on the use of so-called ‘trigger’ packets. |
| strobe | It is used as a port scanner. |
| SLAD | A tool for performing local security checks against GNU/Linux systems. Through this tool you can run the following tools on the target machine: John-the-Ripper, Chkrootkit, LSOF, ClamAV, Tripwire, TIGER, Logwatch, TrapWatch, LM-Sensors, Snort, etc. |
Implementation
OpenVAS needs to be installed on a machine that will act as a network scanning server. You may install OpenVAS Client software on your desktop and connect to the server over the network. The server runs on port 1241. Network firewalls should be configured appropriately to allow scans and administrative traffic of OpenVAS to pass through it. It is also recommended to keep the scanning server in a different network zone than that of your production server.
For effective vulnerability management, you should know the scope, scan frequency, incident management and remediation. There should be a complete list of systems that are within the scope of scanning, along with the scan frequency. Although OpenVAS does not have a feature to automate vulnerability scans, you can still create sessions and save them. Each session can be opened simultaneously and run against available network vulnerability tests.
Incident management will include a formal process of reporting, and informing the security team about security vulnerabilities reported by OpenVAS. You can generate HTML reports through OpenVAS and save them in the session as well as on file servers for the audit trail.
Installation
In order to get started with it yourself, you need to install OpenVAS Server and OpenVAS Client software. OpenVAS Server can be installed by downloading the following software, all of which are available in the order mentioned from relevant websites provided:
- Download and install openvas-libraries
- Download and install openvas-libnasl
- Download and install openvas-server
- Download and install openvas-plugins
- Make and install OpenVAS Server SSL certificate:
# openVAS-mkcert
- Add user to OpenVAS Server
# openVAS-adduser
- Update to latest NVTs:
# openVAS-nvt-sync
- Download and install openvas-client
Now start the OpenVAS Server as follows:
# openVASd -D
…and run the OpenVAS Client as shown below:
# OpenVAS-Client
That’s it! Configure and set it the way you want it…
Wrapping up
There is a need for a vulnerability assessment system to identify potential weaknesses well in time, and to take appropriate action before a malicious user exploits them. OpenVAS is just one of those tools that are a must.
















































































Its nice to have an open source parallel tool for Nessus. Appreciate this article. This is good for beginners. But for real vulnerability assessment one should use Nessus. OpenVAS is not so good in updating new plugins. Where nessus have a really good team for developing plugins for latest vulnerabilities.
I agree with you raj. The project didnt pickedup well like Nessus did. More over if you see the licensing terms of Nessus, you cant use the free version of it for commercial use. So, now it looks like the opensource products are not much in this space, all are commercial. And if you go for commercial products you have others who are much better than Nessus !
Thanks for reading and giving your valuable thoughts on the subject.
-rajender