Contiki is an operating system with a focus on low power IoT devices. Cooja is the Contiki network simulator. Cooja allows the large and small networks of Contiki motes to be simulated. This article takes the reader through the process of programming IoT with Contiki and Cooja.
We are all surrounded by a number of gadgets, mobile devices, smartphones, wireless nodes and many other objects that are digitally connected in real-time. The Internet of Things (IoT) enables real world objects to interact with each other. These objects can share information and communicate in real-time to deliver better performance as well as security. IoT works by developing and integrating smart objects that can be controlled using remote network infrastructure.
The term, the Internet of Things, was coined by Kevin Ashton in 1999. The implementation of IoT is now widespread because of high performance wireless technologies. Radio frequency identification (RFID) tags and sensors are the most important components of IoT. The RFID tags can be embedded in real world devices and objects, which can be monitored remotely using software based applications. RFID readers can be used to locate, read and sense RFID implanted objects. Very small, micro-sized transmitting and receiving chips are integrated with RFID to help them communicate with distant objects.
As per reports from Forbes.com, the market for the Internet of Things is expected to reach around US$ 267 billion by 2020. Analysis from Gartner underlines that around 8.4 billion objects, with investments amounting to US$ 273 billion, will be interconnected with each other in the current year (2017-18). This represents a 31 per cent increase over the figures of 2016-17.
Some of the key applications of IoT include:
- Smart cities, retail points, smart grids, agriculture and farming, homes and offices
- The Internet of Vehicles (IoV)
- Connected cars
- Connected railways infrastructure
- Wearable devices
- Software defined networking
- The industrial Internet
- Energy management

Research domains in IoT
Due to the ever increasing deployment of IoT in the government and in the private sector, there is a need to analyse various factors that can affect its overall performance and efficiency.
The following are some of the key research issues in IoT:
- Security, privacy and trust architectures
- Big Data analysis and scalability
- Device interoperability and compliance
- Robustness and fault tolerance
- Cognitive networking
- Energy aware approaches
- Virtualisation
- Ontology models
Free and open source tools for IoT programming
Featured below are some well known open source tools used for IoT programming.
OpenIoT: This is a free and open source platform to manage and program the sensors on the cloud and the Internet based environment. The concept of Sensing-as-a-Service is being adopted in OpenIoT.
Zetta: This is a free and open source platform that is based on Node.js. Zetta is used to create the IoT servers that can control and run the globally distributed systems, sensors and computers, including those that are on the cloud.
DSA: Distributed Services Architecture is a powerful, open source IoT library that is available for free distribution. It enhances the performance of inter-object communication and makes it very effective. DSA provides the toolkit for managing IoT based applications, services and objects.
Node-RED: This provides the programming interface and APIs for the Internet of Things. Using Node-RED, the flow based creation of remote IoT objects can be done easily with a Web browser based flow editor. In the flow editor of Node-RED, the JavaScript code can be executed and remote objects can be programmed easily with powerful functionalities.
IoTivity: This is a powerful open source library which enables inter-object connectivity with enormous speed and performance. It is written and programmed in C and C++. Most of the performance aware protocols (like ANT+, Bluetooth low energy, Wi-Fi Direct, Zigbee and Z-Wave) can be easily integrated with IoTivity.
There are other open source implementations for the Internet of Things as listed below.
Development toolkits and libraries
- Arduino
- Eclipse IoT Project
- Kinoma
- M2MLabs Mainspring
- Node-RED
- ThingBox
Automation for home and offices
- Eclipse SmartHome
- Home Gateway Initiative (HGI)
- Ninja Blocks
- openHAB
- PrivateEyePi
- RaZberry
- The Thing System
Middleware
- IoTSyS
- Kaa
- OpenIoT
- OpenRemote
Operating systems
- AllJoyn
- Brillo
- Contiki
- FreeRTOS
- Raspbian
- RIOT
- Spark
- TinyOS
IoT integration tools and horizontal platforms
- Canopy
- Chimera IoT
- DeviceHive
- IoT Toolkit
- M2MLabs Mainspring
- Mango
- Nimbits
- Open Source Internet of Things (OSIoT)
- OpenRemote
- Pico Labs
- prpl Foundation
- RabbitMQ
- SiteWhere
- SiteWhere
- ThingSpeak
- webinos
- Yaler
Protocols
- Advanced Message Queuing Protocol (AMQP)
- Constrained Application Protocol (CoAP)
- Extensible Messaging and Presence Protocol (XMPP)
- OASIS Message Queuing Telemetry Transport (MQTT)
- Very Simple Control Protocol (VSCP)
Implementations for engineering
- Open Garden
- Open Source Robotics Foundation
- OpenWSN
Using the Contiki OS with the Cooja simulator to program the IoT
Contiki is a popular, free and open source operating system for IoT programming available under the BSD licence with the base code of the C programming language. Contiki can be used for communication between low powered RFID chips in wireless networks with a high degree of performance and security.
The programming on Contiki is done using the Cooja network simulator, in which the base libraries of RFID chips and sensors are available in C. To program, control and monitor the remote IoT devices, the back-end C programs and related header files can be customised and recompiled to get the desired results. Contiki works on IPv4 as well as IPv6 networking with the integration of lightweight protocols, so that low power chips and radio frequency chips can be connected without performance issues.
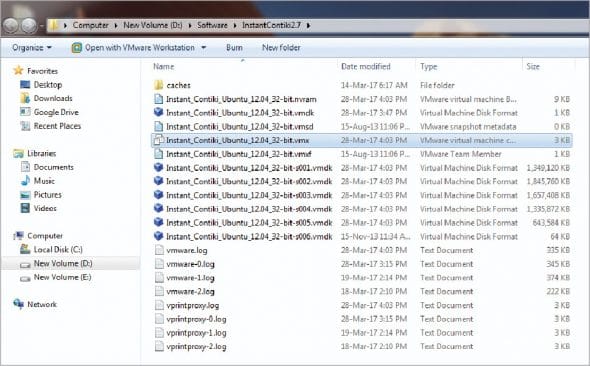
Once the compressed Instant Contiki is downloaded, it can be used on any host operating system. Instant Contiki is available on sourceforge.net as a compressed file which then has to be extracted. The uncompressed or extracted Instant Contiki can be executed on VMware Player, which is a virtualisation tool that can be downloaded free.
In the extracted folder of Instant Contiki, there is the executable file Instant_Contiki_Ubuntu_12.04_32-bit.vmx.
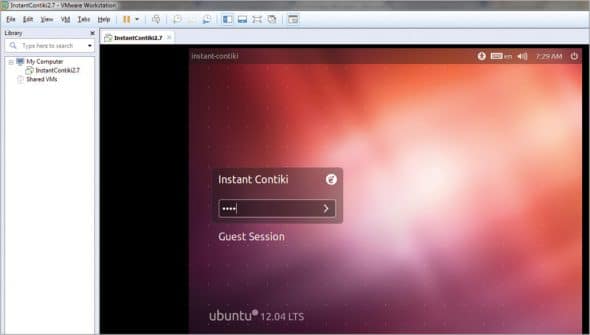
This file, on executing, will automatically open in VMware Player, and we will be ready to work with Contiki using virtualisation software in parallel with any host operating system. The default password for the Contiki operating system is ‘user’.
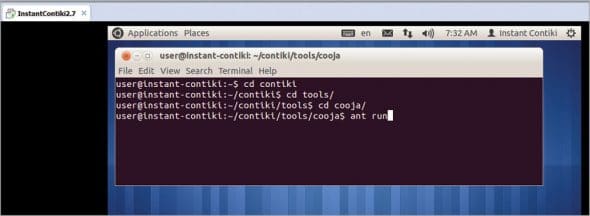
After loading the Contiki OS, the commands given in Figure 3 are executed in the terminal so that the Cooja simulator gets loaded for the implementation of IoT.
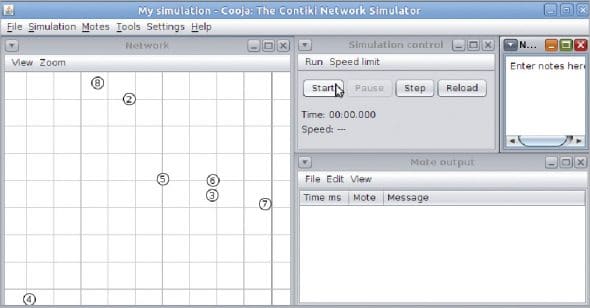
Creating a new network in the Cooja simulator
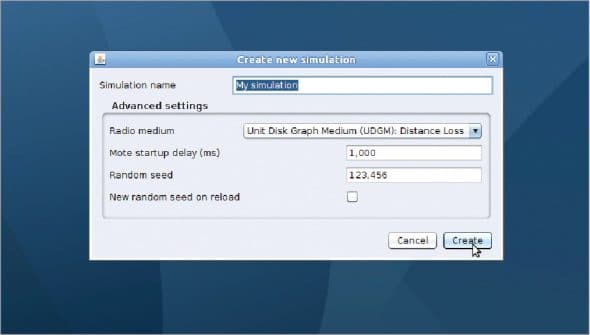
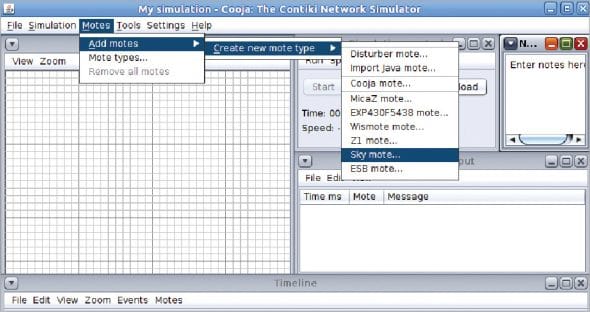
In the file menu of Cooja, select New Simulation as shown in Figure 4.
In the dialogue box, the basic network parameters are set, which include the name of the simulation, radio medium, startup delay and random seed.
Once the basic layout and working environment is ready, you need to import the RFID tags, sensor nodes or any other wireless devices that are to be connected and have to communicate over the IoT. In wireless networking and IoT, these are known as motes. There are many types of motes in Cooja that can be programmed.
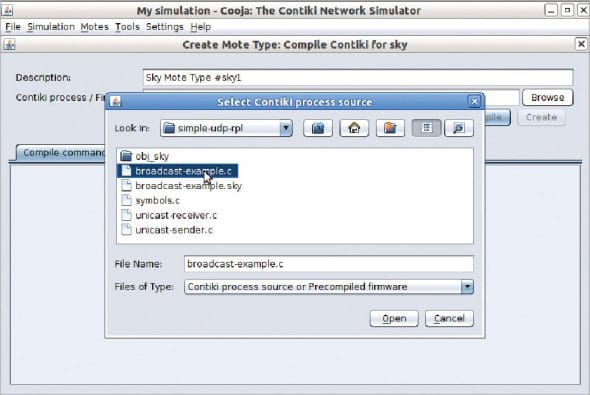
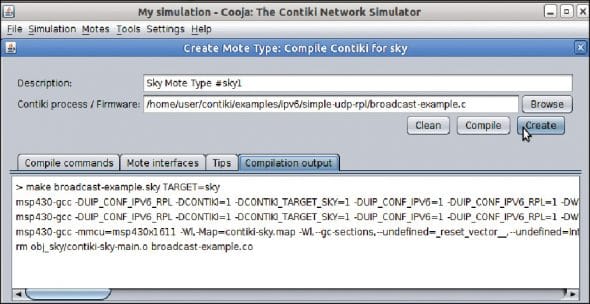
Physical motes, too, can be connected by using ports on the system so that real-time interfacing can be done. Every mote, with the base properties and programming APIs, is specified in the C source code at the back-end of Cooja. These C source code files can be customised and recompiled to get the new or desired output from these motes.
After compiling C code, a number of virtual motes can be imported in the simulation area so that the transmission of radio signals can be viewed and analysed.
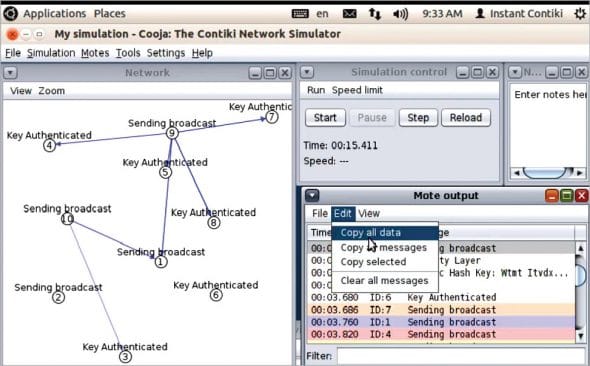
In this simulation of the IoT network, the scenario of a dynamic key exchange between the motes is done. Here, the dynamic security key is generated and authenticated for communication. In the IoT, for reasons of security, it is necessary to devise and implement the protocols and algorithms by which the overall privacy and security in communication can be enforced to avoid any intrusions. As the IoT can be used for military applications, it becomes mandatory to work on highly secured key exchange algorithms with the dynamic cryptography of security keys.
Once the simulation is complete, the network log files, which include the source and destination motes, the time, and the overall activities performed during simulation are analysed. In the Mote Output Window, the log data can be copied and further analysed using data mining and machine learning tools for predictive analytics.














































































Hi,
I want to port contiki on Silicon Labs’ devices.
Please tell me how to start ?
Thanks & Regards
Bipul kumar