Get the feel of software defined networking (SDN) an approach to computer networking that allows admins to manage services by abstracting higher-level functionality. This article explains how to implement an SDN based firewall using SDN controllers in Python.
A firewall is a system that secures incoming network packets, which come from various sources, as well as outgoing network packets. It can monitor and control the flow of data which comes into the network from different sources, and works on the basis of predefined rules.
Firewalls typically maintain a barricade between a confidential, protected internal network and another outside network, such as the Internet, which is assumed not to be secure or trusted. They can be categorised as either hardware or software firewalls. Network firewalls are software programs running on different hardware appliances in the network.
Software based firewalls provide a layer of software on a host, which controls network traffic in and out of that particular machine. Firewall appliances may also provide other functionality to the internal network they protect, such as acting as DHCP or VPN servers for that network.
The system analyses data packets for parameters like layer2 or layer3 switch packet formats. It can also perform deep packet scrutiny for higher layer parameters (like application type and services, etc) to filter network traffic.
Firewalls are an essential component of any secure network communication for bi-directional packet flow.
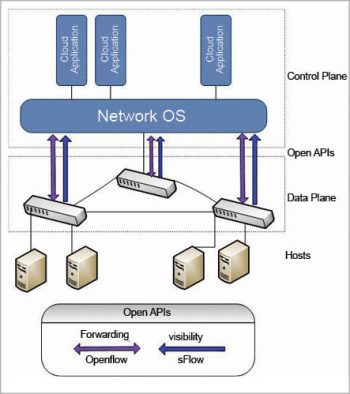
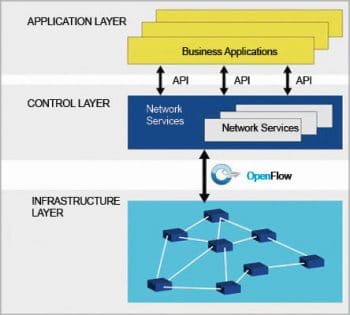
Software defined networking
Software defined networking (SDN) is the new network technology. It emphasises the separation of the network and the control plane. Responsibility is divided between both the planes. The forward plane is only responsible for packet forwarding in the network. The control plane is responsible for policy creation and its implementation, based on predefined rules. It acts as the entry point of the system and can replace the conventional router. Any packet coming into the network is examined by the control plane and a decision is taken on whether to drop the packet or forward it to the next host. It can also update the IP table entry.
Hence, an SDN is the physical separation of the control plane from the data plane. So, instead of each networking device independently forwarding packets to the next hop, the controls are centralised on SDN controllers.
SDN is an engaging platform for network virtualisation, since each occupants control logic can run on a controller rather than on physical switches. It is an approach to computer networking that allows network administrators to manage network services through the abstraction of higher level functionality.
So, SDN networks provide flexibility, programmability and simplicity to network operations. Traffic can be directed, adjusted or personalised without requiring physical wiring changes.
An SDN promises consolidated control and traffic management, which deals with automated network security that is more adaptive and mountable.
The characteristics of SDN are:
- Directly programmable
- Agile
- Centrally managed
- Programmatically configured
- Experimenting and research is not expensive
- Fast upgrades
SDN architecture
SDN architecture is basically focused on allowing network administrators to manage and control the whole network through a software program based controller. This goal is achieved through the separation of the data plane and control plane, which simplifies the networking services.
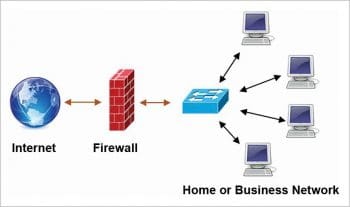
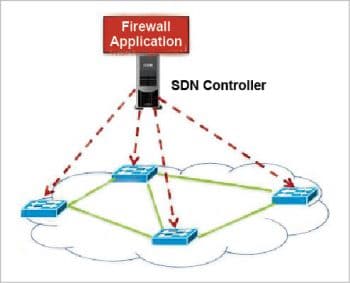
Traditional vs SDN based firewalls
Here are a few differences between traditional and SDN based firewalls:
- Internal traffic is not seen and cannot be filtered by a traditional firewall.
- An SDN based firewall works both as a packet filter and a policy checker.
- The first packet goes through the controller and is filtered by the SDN firewall.
- The subsequent packets of the flow directly match the flow policy defined in the controller.
- The firewall policy is centrally defined and enforced at the controller.
Implementing an SDN based firewall
A firewall is used as a barrier to protect networked computers by blocking malicious network traffic generated by viruses and worms.
In this article, I have implemented an SDN based firewall by writing code for an SDN controller in Python. More specifically, I have written code to add firewall rules to a POX controller.
The implementation of an SDN based firewall requires the installation of Mininet and the POX controller. Both are open source tools and are freely available. For the installation and startup, please refer to my article at the following URL: https://www.opensourceforu.com/2015/10/mininet-an-emulator-for-prototyping-large-network-topologies-on-a-single-machine/. This article helps you to understand and work with Mininet. It emphasises the creation of a simple network topology using POX in Python.
In this article, I have implemented a layer 2 firewall that runs alongside the physical address based module on POX runtimes. The firewall application is provided with a list of MAC address pairs, i.e., an access control list (ACL). When a connection gets established between the controller and the switch, the application installs static flow rule entries in the OpenFlow table to disable all communication between each MAC pair.
Examples of a few firewall rules
At the specified switch, block all traffic coming from host 10.1.1.1:
00-00-02-00-00-00-00-00 BLOCK srcip=10.1.1.1
At the specified switch, block all traffic coming from host 10.1.2.2, if the packets TOS is marked with 32 and its destined for 10.1.3.1:
00-00-03-00-00-00-00-00 BLOCK srcip=10.1.2.2 dstip=10.1.3.1 tos=32
At the specified switch, redirect traffic destined for 10.1.2.1 and, instead, send it to 10.1.2.2:
00-00-01-00-00-00-00-00 REDIRECT dstip=10.1.2.1 TO 10.1.2.2
At the specified switch, mark the TOS field of all packets sent by 10.1.1.1 with value 40:
00-00-04-00-00-00-00-00 MARK srcip=10.1.1.1 TOS 40
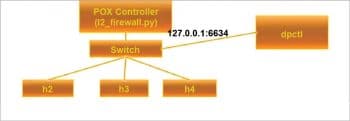
Firewall execution in SDN
Check the MAC address against the firewall rules available in the POX controller.
- Is transparent=False, and either Ether type is LLDP or the packets destination address is a Bridge Filtered Address? If yes, DROP.
- Is the destination multi-cast? If yes, FLOOD.
- Install the flow table entry in the switch so that this entry will be used when a similar packet reappears.
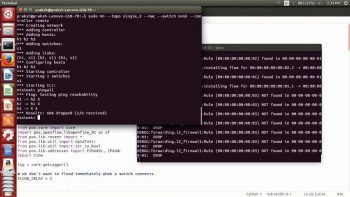
To start this, you will find a skeleton class file at pox/pox/misc/l2_firewall.py. This is currently not blocking any traffic and you will need to modify this skeleton code to add your own logic later. Here, I have added some rules to block the packet from a specific address. To test the firewall, put the l2_firewall.py in the pox/pox/misc directory and run the POX controller as shown below:
./pox.py log.level --DEBUG forwarding. l2_firewall
The above code runs the firewall on the POX controller and filters the traffic by the rules specified in it.
After the connection between the controller and the switch is established, we can verify the connectivity between all pairs of hosts by typing pingall in the Mininet console. Note that when ping cannot get through a pair of hosts, you need to wait for the timeout, which takes about 10 seconds.
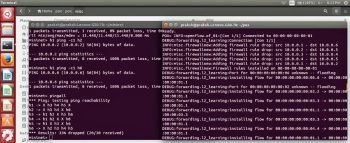
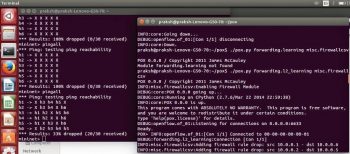
The execution on an SDN based firewall is shown in Figures 6 and 7.
As shown in Figure 6, Mininet creates a network with three hosts. I have run it on one terminal. In another terminal, the POX controller is executed with the l2_firewall.py file, which works as the firewall and filters the traffic as per the rules specified in it.
As shown in Figure 7, I have tested the firewalls rules with the pingall command, which runs on one terminal to check the connectivity with all the hosts of the network. The result indicates that one host cannot connect with the other, which can be added as a drop packet rule in the firewall.
You, too, can add rules using the CSV file. So is very easy to modify the rules for packet drops by just changing rules in the CSV files.
In this article, I have tried to demonstrate an SDN based firewall, which has many advantages over the traditional variants. The firewall in SDN is controlled by the central controller rather than the individual device. Also, it is a software based firewall so theres no need for any extra device. The updating rules are also easy to make.













































































[…] networks are becoming a standard for businesses. With the high penetration of open source projects, the automated network is […]